
What is Threat Hunting?
Threat Hunting is a creative process. One’s abilities to think abstractly, challenge ideas, and be unafraid of failure lead to more knowledge and breakthroughs than someone who does everything the same way every time.

Threat Hunting is a creative process. One’s abilities to think abstractly, challenge ideas, and be unafraid of failure lead to more knowledge and breakthroughs than someone who does everything the same way every time.

The cyber kill chain is an adaptation of the military’s kill chain, which is a step-by-step approach that identifies and stops enemy activity.
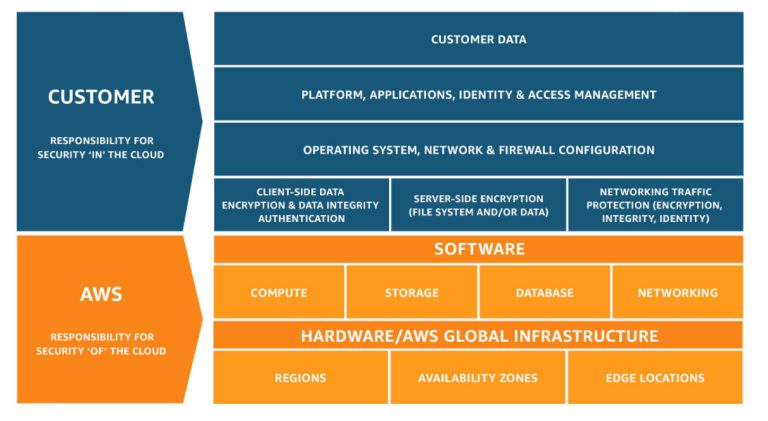
Security and Compliance is a shared responsibility between AWS and the customer. This shared model can help relieve the customer’s operational burden as AWS operates, manages and controls the components from the host operating system and virtualization layer down to the physical security of the facilities in which the service operates.

The Adversarial Tactics, Techniques, and Common Knowledge or MITRE ATT&CK is a guideline for classifying and describing cyberattacks and intrusions.

Threat modeling is the process of adopting a strategic, risk-based approach to identifying and resolving your security blind spots.

Quick overview of the CIS (Community Defense Model) CDM.

Formerly the SANS Critical Security Controls (SANS Top 20) these are now officially called the CIS Critical Security Controls (CIS Controls).
Get email alerts when we publish new blog articles!