ISO 27001 certification is among the most popular security certifications. The standard is internationally accepted and considered to provide a more robust security framework than other standards (such as SOC 2).
The ISO 27001 standard possesses considerable overlap with other security frameworks (such as NIST, CIS, etc.), and it can be used to satisfy the requirements of government regulatory bodies such as HIPAA. Furthermore, if your organization already has an SOC 2 Type 2 report, you already meet about 60% of ISO 27001 requirements.
This article is designed to be used as a reference only. While most security controls are straightforward to understand, implementing an Information Security Management System and getting through the certification process can be complex and time-consuming.
For those coming out of a SOC 2 audit and looking at ISO 27001 to strengthen their compliance posture, there are several major differences and steps that need to be highlighted: The implementation of a real Information Security Management System (ISMS), the Statement of Applicability / Annex A Controls, internal audits, management reviews, and a different validation/life cycle of the ISO process.
It is advisable that organizations seek the assistance of professional compliance consulting companies, especially if they are navigating through the certification process for the first time.
Implementation Plan
A high level implementation plan for achieving ISO 27001 certification can be seen in the following diagram. This blog article will reference this diagram whenever appropriate.
Diagram 1: ISO 27001 implementation steps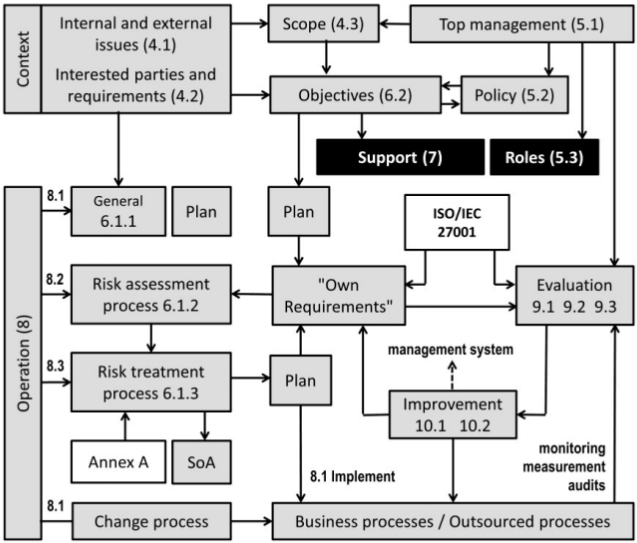
Diagram 1: ISO 27001 implementation steps
We try to break the process down into easy to understand and follow steps.
Step 1: Get familiar with the ISO standards
To get familiar with the standard, we encourage you to start by obtaining a copy of the ISO/IEC 27001 standard. In addition, you can opt in to get a copy of the supplementary ISO 27002 so that you can learn all about the controls needed in depth.
You can buy the ISO 27001 from here and the ISO 27002 from here.
Step 2: Appoint a Security Officer
If you plan on going through the certification process on your own, you will need to appoint an information security officer (or a comparable role) and assign responsibilities and authorities to this role to ensure that the management system meets the requirements (section 5.3 in Diagram 1).
Step 3: Appoint a Project Leader
Appoint a project leader (this may be the security officer mentioned above or another individual) and create a project plan.
* Make sure to get the necessary resources for the project (7.1).
* (Re)organize your document management (7.5).
Step 4: Determine starting points
* Perform a context analysis (4.1 and 4.2).
* Use the outcome of the context analysis to determine the scope of your management system (4.3).
* Determine all outsourced processes within the scope (8.1).
* Determine the risks for the management system as a whole and implement actions to address these risks (6.1.1).
Step 5: Define processes
* Define a process for risk assessment that meets the requirements of the Standard and your own requirements (6.1.2).
* Define a process for risk treatment that meets the requirements of the Standard and your own requirements (6.1.3).
* Define a process for managing competence that meets the requirements of the Standard and your own requirements (7.2).
* Define a change-management process that meets your own requirements (8.1).
* Determine which processes must be monitored and measured and how this must take place (9.1).
* Determine an audit program and define a process for conducting internal audits (9.2).
Step 6: Initial risk assessment
* Perform the initial organization risk assessment process as outlined in Step 5. The results of this initial assessment give you an impression of the current status of your information security risks (6.1.2).
* Follow the risk treatment process defined in step 5 and determine the necessary controls (6.1.3).
* Compare the controls that you have determined with those in Annex A and produce a Statement of Applicability (6.1.3).
* Formulate a risk treatment plan for unacceptable risks.
* Obtain risk owner’s approval for this plan and risk owner’s acceptance of the residual risks (6.1.3).
Step 7: Establish policy and objectives
* Establish an information security policy (5.2). Take the results of the initial risk assessment into account.
* Establish measurable information security objectives (6.2). Take the results of the initial risk assessment into account (6.2c).
* Publish and communicate your information security policy (5.2).
* Determine which information security objectives should be monitored and measured and how this should take place (9.1).
* Develop awareness training for all persons doing work under the organization’s control (7.3).
* Request quotes from accredited certification bodies (auditors) and choose a date for the certification audit
Step 8: Implement, monitor and measure
* Implement your risk treatment plan (6.1.3/8.3).
* Implement your communication plan (7.3).
* Make a schedule for all necessary actions and monitor this schedule (8.1).
* Determine which processes should be monitored and measured and how this should take place (9.1).
* Determine which controls should be monitored and measured and how this should take place (9.1).
* Start using your process for managing competence (7.2).
* Organize awareness training for all persons doing work under the organization’s control (7.3).
Step 9: Collect evidence of performance
* Ensure that processes, controls, and plans are monitored and measured, and retain documented information as evidence of the results (9.1).
* Perform a full internal audit and retain documented information as evidence of the results (9.2).
NOTE: The internal audit is done by independent of the process personnel, 3rd party consultant or an outside company.
Step 10: Correct nonconformities
* Correct all established nonconformities and, where possible, remove the causes of nonconformities (10.1).
* Make necessary improvements to the management system (10.1 and 10.2).
Step 11: Management review
* Prepare a management review (9.3) – collect relevant information about the management system and think of questions that can be submitted to top management to have your management system reviewed.
* Ensure that all review comments, decisions, and necessary actions are documented.
* Plan and perform the actions that (possibly) come from the management review.
Step 12: Preparation for the certification audit
To be able to demonstrate that your management system is effectively implemented and maintained, it is advisable to perform an additional risk assessment at this time, so that you can compare the results of this assessment with the results of your first assessment (see step 5 & 6). If all went well, your information security management system has made a positive contribution to the development of your information security risks.
By carrying out the previous steps, your management system has gone through the entire Plan-Do-Check-Act (PDCA) cycle. This is an important prerequisite for being eligible for certification. From now on, keep applying your information security management system according to your own requirements, and keep improving the system continually. Put all documentation in order and collect evidence in preparation for the certification audit.
Certification Process
A certification audit is an audit performed by an accredited certification body to certify the management system of an organization. Certification of a management system provides independent demonstration that the management system of the organization:
* conforms to specified requirements;
* is capable of consistently achieving its stated policy and objectives;
* is capable of ensuring the client meets applicable statutory, regulatory and contractual requirements;
* is effectively implemented.
Certification body (CB) also known as Auditors or Auditing Team
To have your information security management system certified, you must invite an accredited certification body (CB). In most countries, multiple CBs are active. Only an accredited certification body can issue a “real” ISO/IEC 27001 certificate. You can recognize a “real” certificate by the CB’s accreditation number, which you can also find on the website of the institution that granted the accreditation. Approximately ninety countries throughout the world have a national accreditation body (AB). A list of ABs can be found at this website: https://www.iaf.nu. Each AB guarantees that interested parties can have justified confidence in all certificates issued under its supervision. All national ABs are affiliated with the IAF (International Accreditation Forum).
A CB can be accredited by multiple ABs, as long as the ABs are registered with the IAF. To be accredited, a CB must meet a large number of requirements. The AB conducts audits to check whether all requirements are met. The requirements that a CB must meet are not relevant to you, with a few exceptions. For example, this book mentions the requirement that a CB may not issue an ISO/IEC 27001 certificate to a customer if he has not performed a full internal audit or a management review (see clauses 9.2 and 9.3). Another example is the additional requirements imposed on the scope (see clause 4.3). A CB can set additional requirements for your management system. For example, a CB may require that your system is first applied for a minimum time before a certification audit can be performed (to prevent there are too few results that can serve as proof of the effectiveness of the management system). Additional requirements can usually be found in the agreement with your CB.
➢ An accreditation body may attend a certification audit to check the performance of the CB auditor or the CB audit team. This is always done in consultation with the customer.
Initial certification audit
The initial certification audit is an audit that must be conducted in order to receive an ISO/IEC 27001 certificate for the first time. Below is a brief description of the certification process to be used for an initial audit. Every CB must follow this process, although the implementation can sometimes differ.
➢ Please note: for certificate audits, there are many more details than described below.
The initial certification audit of an ISO/IEC 27001 management system must always take place in two parts: Stage 1 and Stage 2.
INITIAL CERTIFICATION AUDIT: STAGE 1
Stage 1 is a preliminary investigation, the CB hereby assesses whether the degree of implementation of the management system indicates that you are ready for stage 1.
Stage 1 is sometimes referred to as the “documentation audit” because the emphasis is often on assessing the documentation of the customer. In reality, reviewing documentation is just one of the activities to achieve the objectives of stage 1. Other mandatory activities are “review the client’s status and understanding regarding requirements of the Standard”, “evaluate the client’s site-specific conditions,” and “undertake discussions with the client’s personnel to determine the preparedness for stage 2”.
In other words, stage 1 goes further than just reviewing documentation. The CB is required to provide a documented audit report with conclusions and identified weaknesses.
When determining the interval between stage 1 and stage 2, you must take into account what you need to do in order to eliminate the points of concern identified during stage 1. The results of stage 1 are assessed by an authorized committee within the CB. The decision can lead to the postponement or cancellation of stage 2.
INITIAL CERTIFICATION AUDIT: STAGE 2
The purpose of stage 2 is to evaluate the implementation, including effectiveness, of the client’s management system. During the stage 2 of the initial audit, the implementation of controls that were determined as necessary by the client (as per the SoA) will be reviewed.
How controls are expected to perform may, for example, be specified in your procedures or policies. At the end of stage 2, the auditor or audit team will analyze all information and evidence gathered during stage 1 and stage 2 to review the audit findings to determine the conclusions of the audit. In a closing meeting, the auditor must present the audit conclusions to you in an understandable manner, including the recommendation of whether or not to grant certification. Stage 2 is sometimes referred to as the “implementation audit.”
This stage of the initial audit is indeed about assessing the implementation of the management system, but also about assessing its effectiveness. For example, stage 2 also involves an assessment of “the client’s management system ability and its performance regarding the meeting of applicable statutory, regulatory and contractual requirements”. In other words, the management system must not only be implemented but also be able to achieve certain results.
AUDIT FINDINGS
During a certification audit, an auditor can determine that you do not fully meet a requirement. The following nonconformities can be distinguished:
* A major nonconformity: this is a nonconformity that affects the capability of the management system to achieve the intended results.
* A minor important nonconformity: this is a nonconformity that does not affect the capability of the management system to achieve the intended results.
Note: a number of minor nonconformities associated with the same requirement or issue could demonstrate a systemic failure and thus constitute a major nonconformity.
During a certification audit, you will not receive any advice regarding your management system. An auditor may present opportunities for improvement during audits, but may never recommend specific solutions— neither orally nor in audit reports. If you need advice, you should seek this from an adviser/consultant/3rd party.
INITIAL CERTIFICATION AUDIT: AUDIT REPORT
The auditor must provide you with a written report of the audit. The report shall also contain:
* a statement on the conformity and the effectiveness of the management system together with a summary of the evidence relating to:
a) the capability of the management system to meet applicable requirements and expected outcomes and
b) the internal audit and management review process;
* a conclusion on the appropriateness of the certification scope;
* a confirmation that the audit objectives have been fulfilled.
In the audit report, the auditor will require you to analyze the cause and describe the specific correction and corrective actions taken (or planned to be taken) to eliminate detected nonconformities within a defined time.
INITIAL CERTIFICATION AUDIT: AUDIT DECISION
After receiving the correction plan drawn up by you, the auditing team (CB) determines whether the proposed corrections and deadlines are acceptable. You will be informed if an additional full audit, an additional limited audit, or documented evidence (to be confirmed during future audits) is needed to verify effective correction and corrective actions.
Each auditor (CB) must have a process to conduct an adequate review before deciding on granting certification. After a positive decision from the auditor (CB), you will receive the ISO/IEC 27001 certificate, and you will become a “certificate holder” – something you can be proud of !
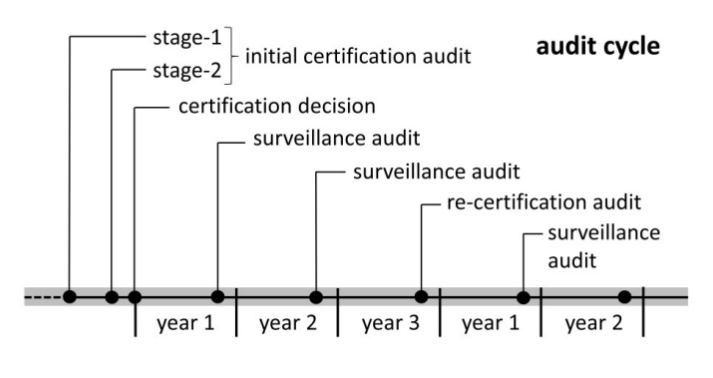
THE 3 YEAR AUDIT CYCLE
After obtaining the ISO/IEC 27001 certificate, a 3-year certification cycle starts, of which your certificate document states the start and expiry date. Surveillance audits are performed in the first and second years following the certification decision. A recertification audit is performed in the third year before the expiration of certification. Subsequent cycles begin with the re-certification decision.
Obtaining a certificate is one thing, but maintaining it is just as important. Keep this in mind while implementing the management system by logically setting up your documentation and not making everything more difficult than necessary.
➢ An auditor (CB) can revise the audit cycle program if necessary — for example, after receiving complaints about an organization, when there are points of concern from relevant interested parties, or at changes in accreditation, certification, or legal requirements. However, this rarely happens in practice.















